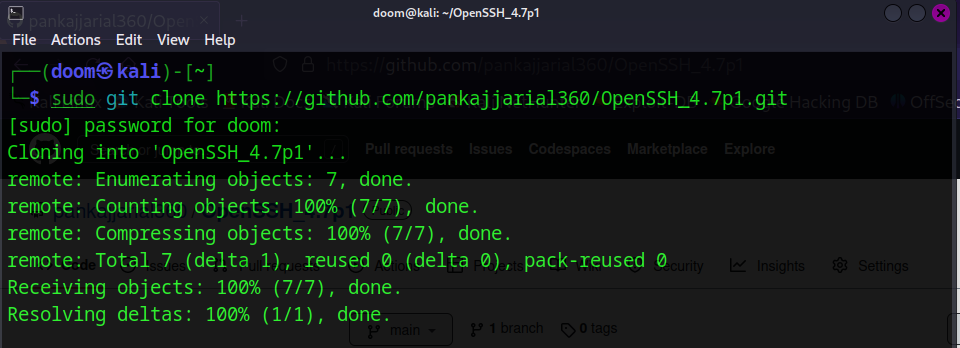
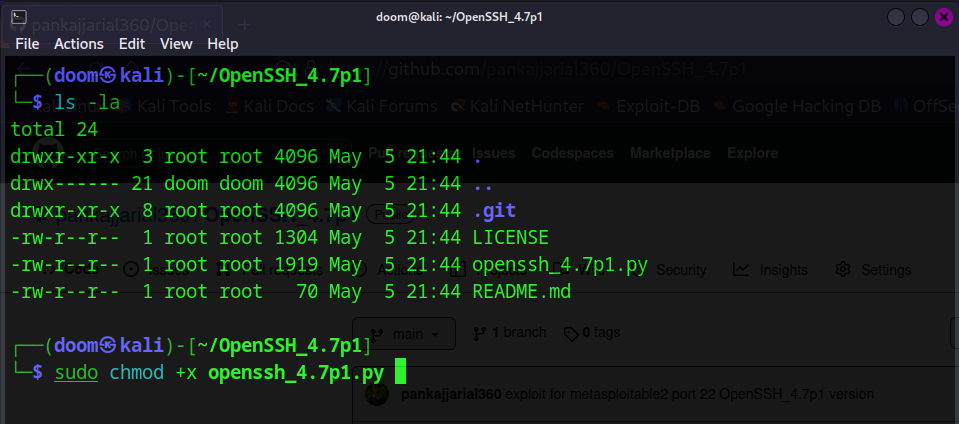
The script first checks the version of the target SSH service to confirm that it is running OpenSSH version 4.7p1. If the version is correct, the script sets up the necessary parameters for the brute-force attack using a list of usernames and passwords from a wordlist file. The script then launches the exploit and waits for it to complete.
Once the exploit is completed, the script retrieves any active sessions that have been created and enters an interactive mode that allows the user to interact with the session.
To use this exploit, you must have the Metasploit Framework installed and configured on your system. You will also need to have a target system with OpenSSH version 4.7p1 installed and running.